This article explains how to allow apps through controlled folder access with Microsoft Defender Antivirus in Windows 11.
Controlled folder access helps protect your valuable data from malicious apps and threats like ransomware.
Occasionally, an app that is safe to use will be identified as harmful and blocked from accessing protected folders with Microsoft Defender Antivirus. When that happens, you can add the app to the list of safe or allowed apps to prevent it from being blocked next time.
Adding apps to access protected folders can help protect your data since only known apps can go through Microsoft Defender Antivirus-controlled folder access. Ransomware apps will also be blocked by default, preventing your data from being encrypted and locked by bad actors in Windows 11.
How to allow apps through controlled folder access in Windows 11
As mentioned above, Controlled folder access helps protect your valuable data from malicious apps and threats, such as ransomware.
You can add apps that are being blocked to protected folders in Windows 11. Below is how to configure apps for access.
Allow apps through the controlled access folder:
In the search box on the taskbar, type Windows Security and select Windows Security in the results list.
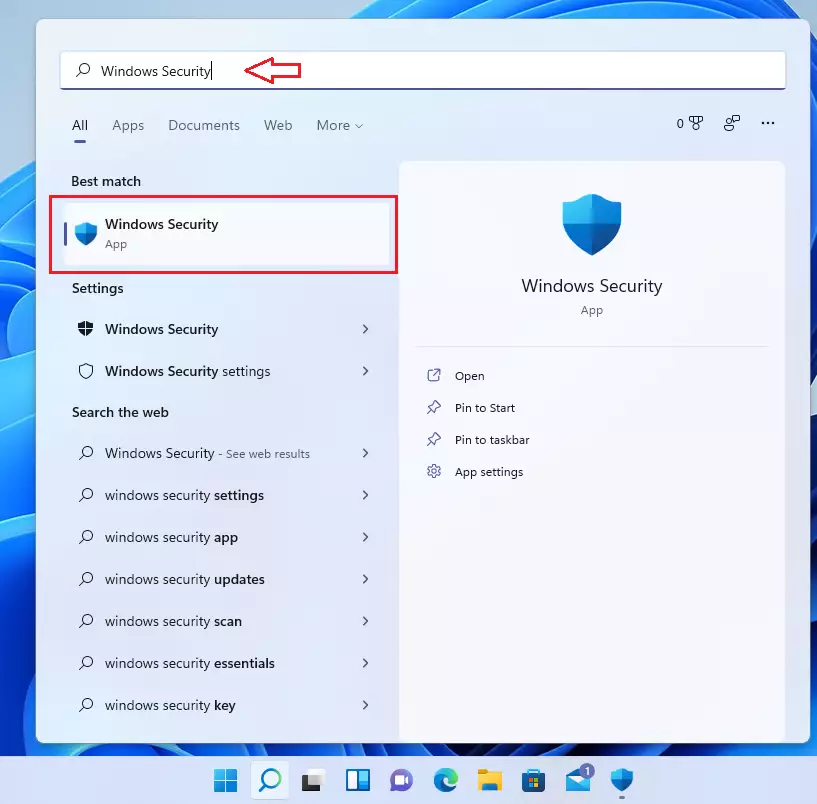
In Windows Security, select Virus & threat protection.
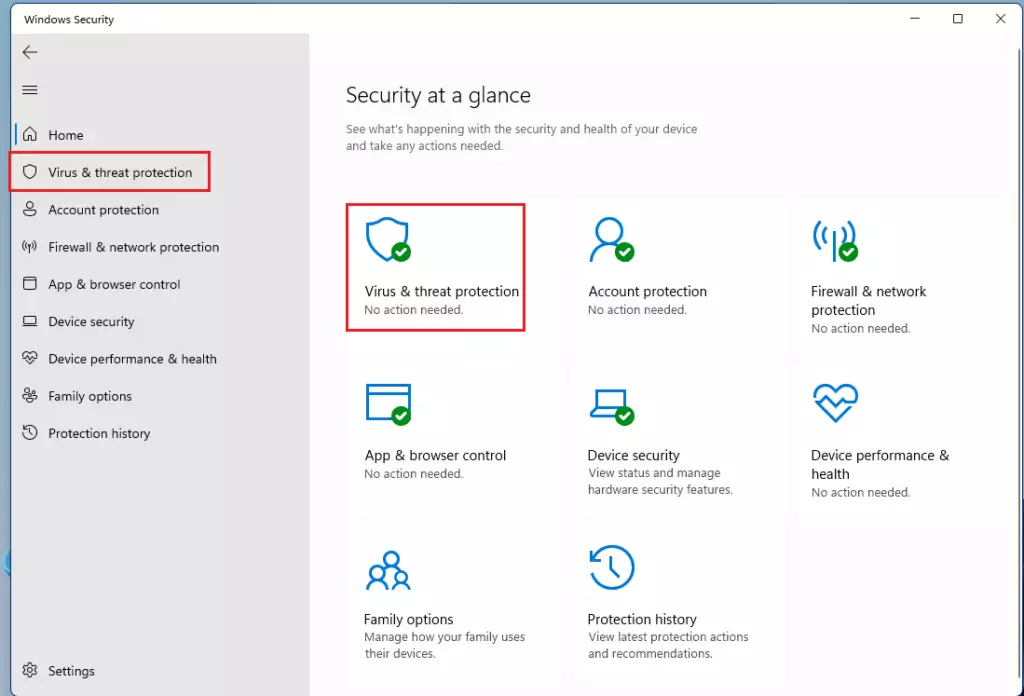
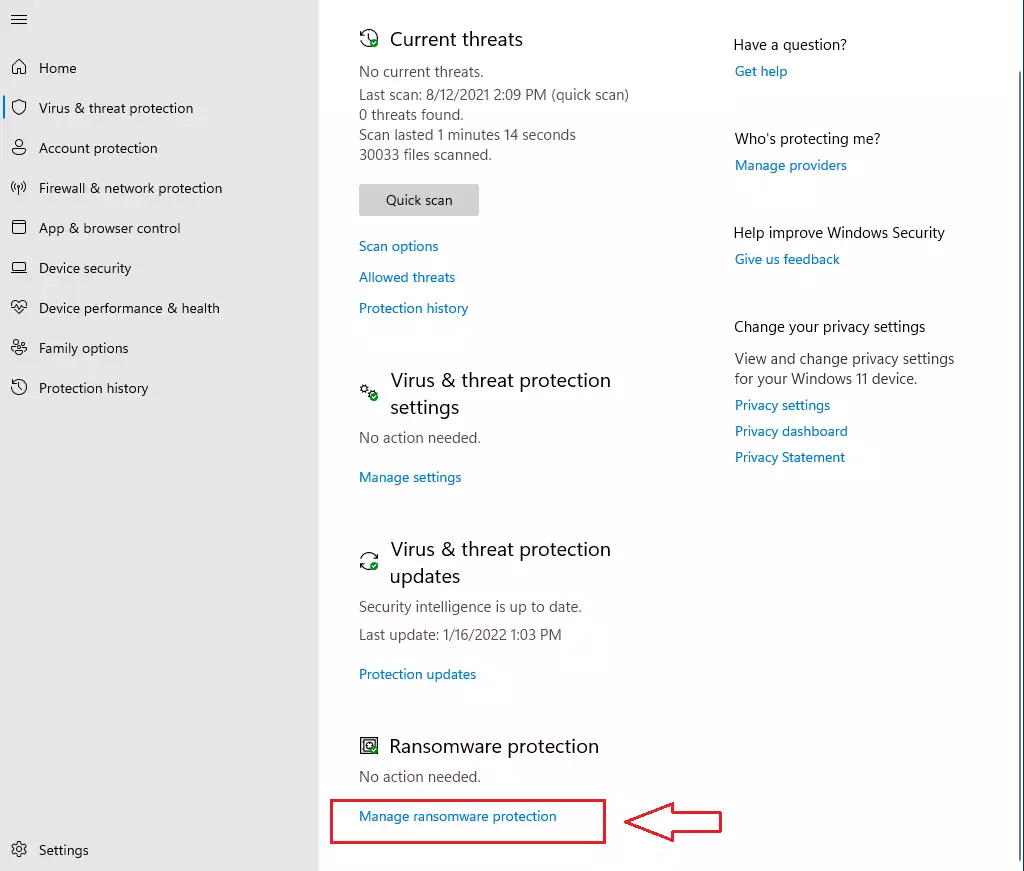
On the Virus & threat protection settings page, under Ransomware protection, select Manage ransomware settings.
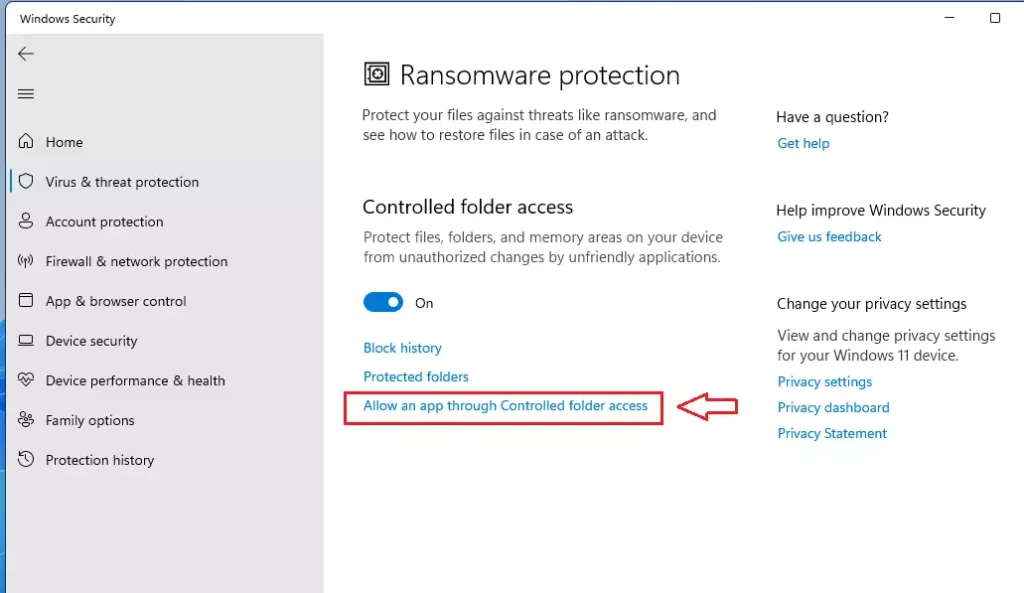
Change the Controlled folder access setting to On or Off.
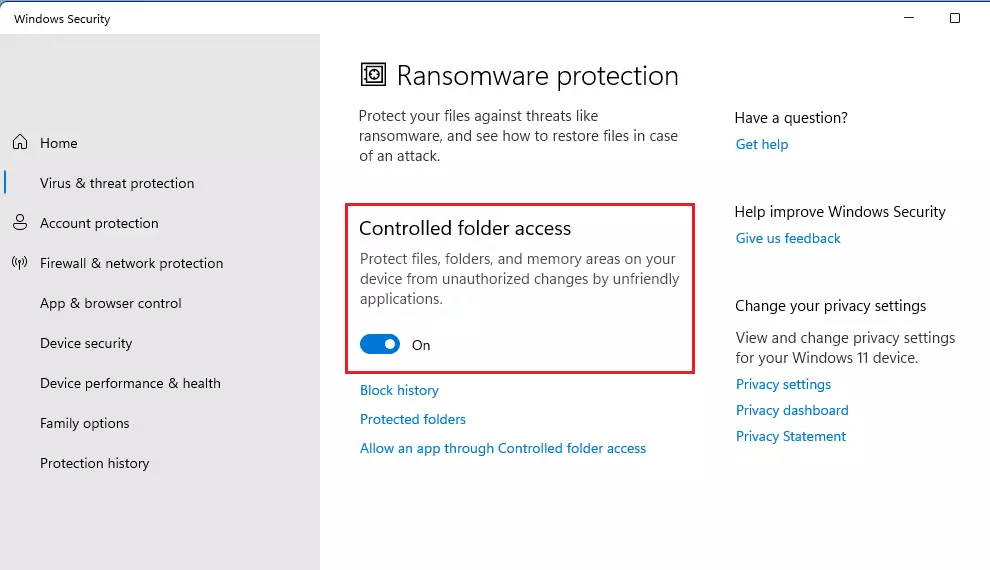
Under Controlled folder access, click on the link that reads: Allow an app through Controlled folder access as highlighted below:
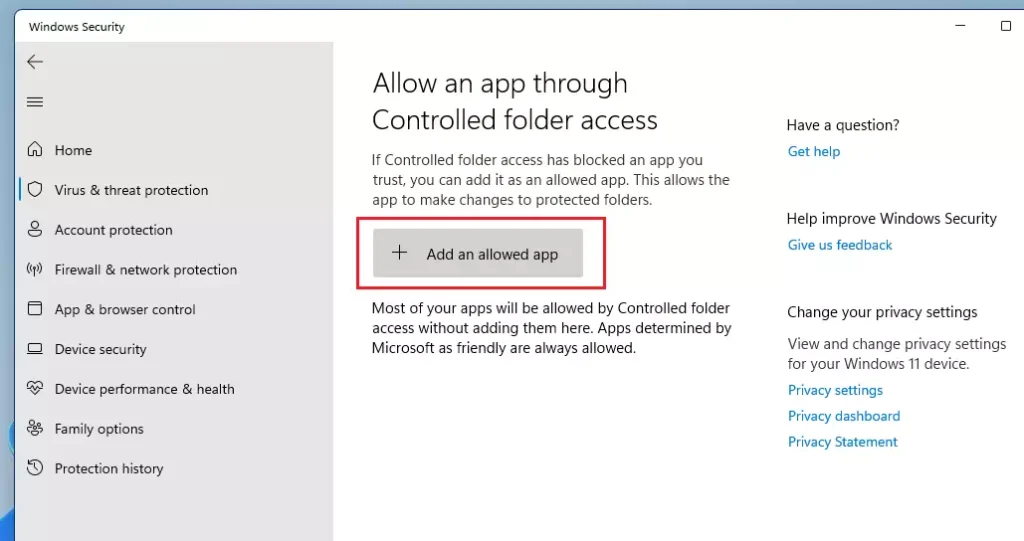
Click on Add a protected folder button, navigate to and select the program executable you want to add, and click on Open.
To remove a folder from the list, select it and click Remove.
How to turn on or off cloud-delivered protection in Group Policy
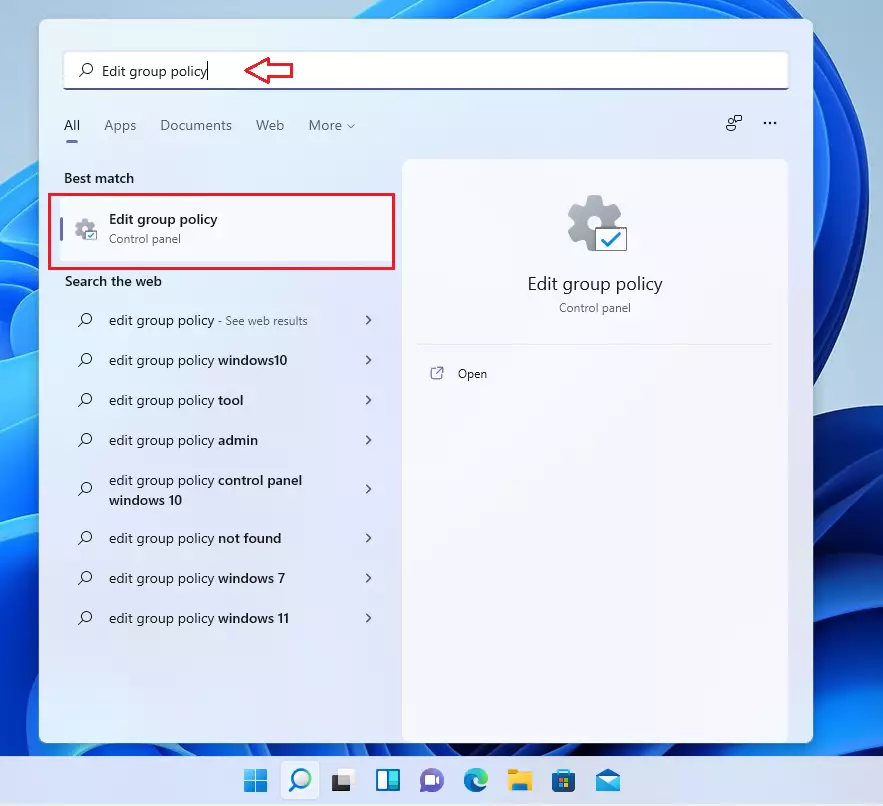
In Windows 11, open Local Group Policy Editor by clicking on the Start menu and searching for Edit group policy, as highlighted below. Under Best match, select Edit group policy to launch Local Group Policy Editor.
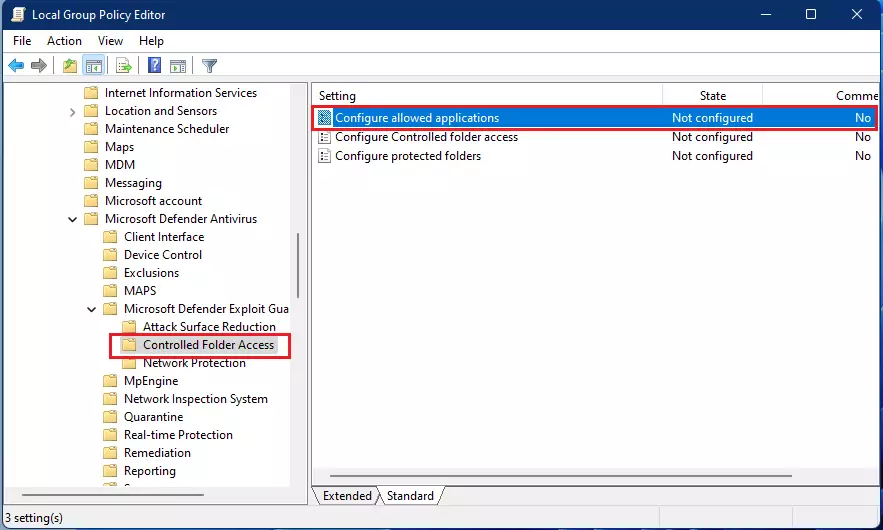
In the left pane of Local Group Policy Editor, expand the tree:
Computer Configuration>Administrative Templates>Windows Components>Microsoft Defender Antivirus>Microsoft Defender Exploit Guard>Controlled folder access
Then, in the Controlled Folder Access details pane on the right, locally and double-click Configure allowed applications.
Set Configure allowed applications setting option to Enabled.
In the options section, specify one of the following: Select Show and each folder you want to protect.
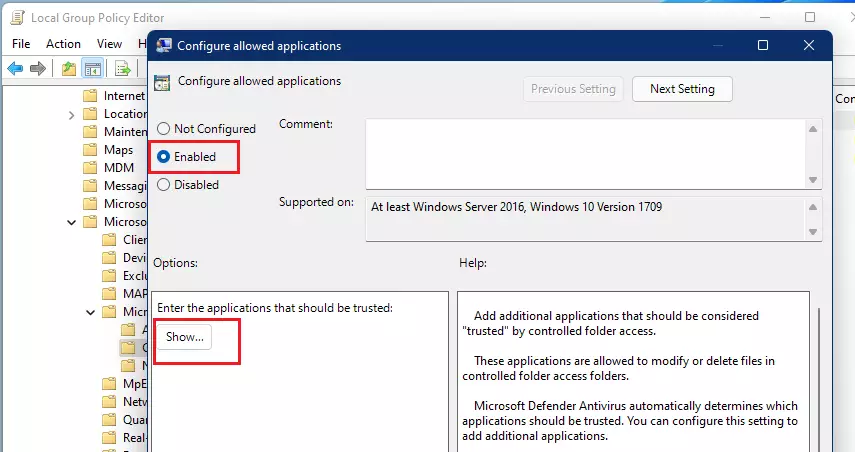
Specify each folder you want to protect on each line. An example is listed below. Enter the path of the folder under the Value name, and the Value data should be 0.
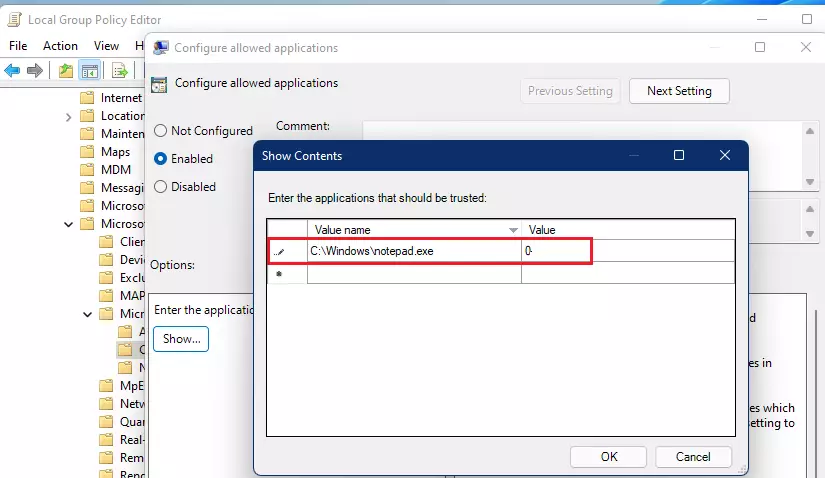
Select OK.
Close Local Group Policy Editor.
That should do it!
Conclusion:
- Controlled folder access is an essential feature in Windows 11 that protects your files from malicious apps, including ransomware.
- Adding safe apps to the list prevents them from being blocked, maintaining your workflow while ensuring data security.
- Follow the outlined steps to manage app permissions and protected folders easily.
- Regularly check and update the allowed apps list to keep your system safe from new threats.
- Familiarize yourself with the Windows Security app and Local Group Policy Editor for comprehensive control over your device’s security settings.


Leave a Reply