This article explains how to prevent installing or moving apps on non-system drives in Windows 11.
There are two main types of apps one can install in Windows. Apps from the Microsoft Store and standalone apps that are packaged with their installers, typically from third-party vendors.
By default, apps from the Microsoft Store are installed on the C: drive of the Windows system. Users can choose to move apps already installed from the Microsoft Store to a different internal or external local drive if they wish.
Users can choose to install new apps on internal or external drives in Windows 11.
If you want to prevent users from installing apps on non-system drives, you can disable this feature using either Group Policy or the Registry Editor.
Disable installing apps on non-system drives using GPO
To access the local group policy editor and make this change, follow the steps below.
First, open the Local Group Policy Editor (gpedit.msc). (Search for “Edit group policy”) on the Start menu.
Then, navigate the folders below:
Computer Configuration > Administrative Templates > Windows Components > App Package Deployment
In the App Package Deployment details pane on the right, locate and double-click the “Disable installing Windows apps on non-system volumes” settings.
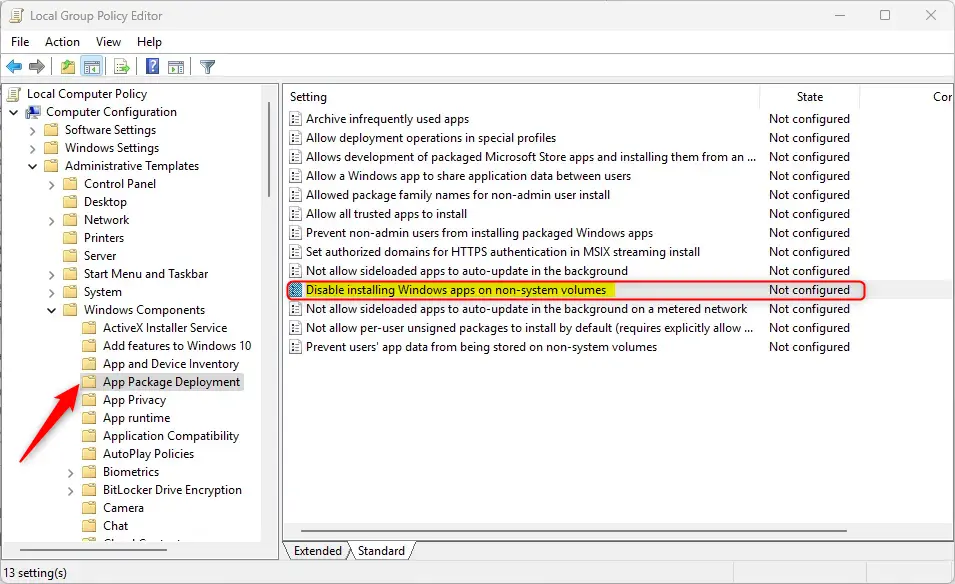
On the “Disable installing Windows apps on non-system volumes” window, set the option to Not Configure, Enabled, or Disabled.
- Not Configured (default) – Same as Disabled.
- Enabled: You can’t move or install Windows apps on volumes that are not the system volume.
- Disabled: You can move or install Windows apps on other volumes.
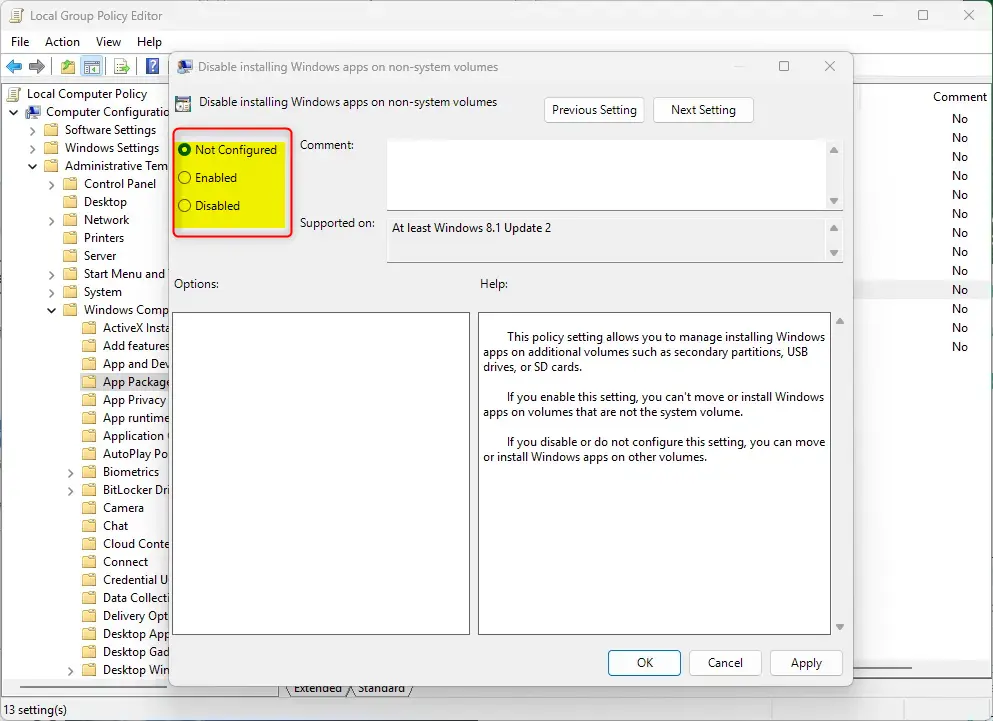
Click OK to save your changes.
Prevent the installation of apps on non-system drives using the Registry
Another way to prevent installing apps on non-system drives is to use the Windows Registry Editor.
Remember to back up your registry before making any changes or create a System Restore point as a precaution.
First, open the Windows Registry and navigate to the folder key path below.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Appx
Right-click Appx > New > DWORD (32-bit) Value and name the new DWORD RestrictAppToSystemVolume.
Double-click RestrictAppToSystemVolume to open it. Then, type 1 to prevent installing apps on non-system drives.
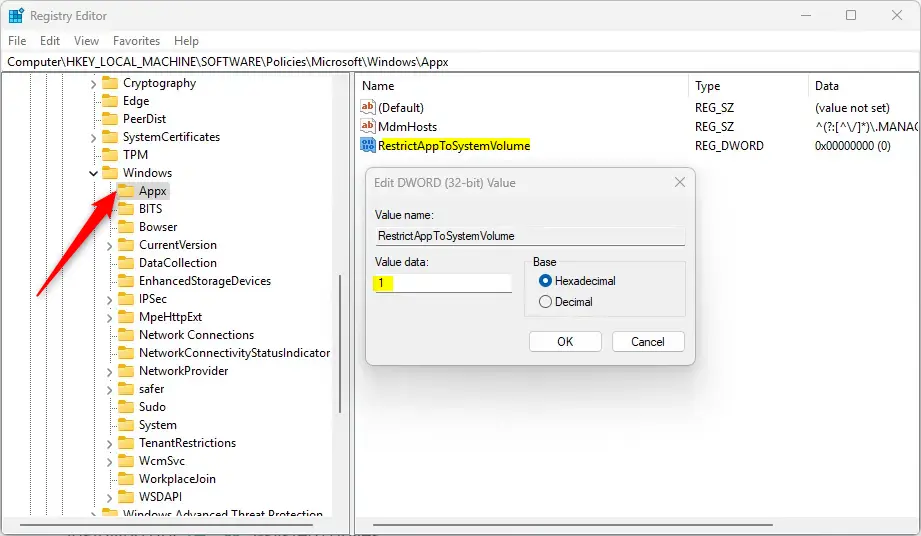
To restore the default behavior and allow users to continue to install apps on non-system drives, delete the RestrictAppToSystemVolume name created above.
RestrictAppToSystemVolume
You may have to reboot your computer to apply the changes.
That should do it!
Conclusion:
In summary, preventing the installation or movement of apps on non-system drives in Windows 11 can be effectively managed using either Group Policy or the Registry Editor. Here are the key takeaways:
- Two App Types: Understand that applications can be from the Microsoft Store or standalone installers.
- Default Behavior: Apps are installed on the C: drive, but users can move or choose other drives.
- Group Policy Method: Utilize the Local Group Policy Editor to disable installations on non-system drives.
- Options include Not Configured, Enabled, and Disabled.
- Registry Method: Modify the Windows Registry to restrict app installations to the system volume.
- Create a DWORD named RestrictAppToSystemVolume and set its value to
1.
- Create a DWORD named RestrictAppToSystemVolume and set its value to
- Backup Precautions: Always back up your registry or create a System Restore point before making changes.
- Reboot Requirement: A reboot may be necessary for changes to take effect.
By following these steps, you can maintain control over where apps are installed on your Windows 11 system.

Leave a Reply