This brief tutorial shows students and new users how to block external extensions from being installed in the Microsoft Edge browser with Windows 10.
The new Microsoft Edge browser has adopted the Chromium open-source project code base, offering better web compatibility and performance over the legacy Edge.
Microsoft Edge browser is cross-platform and supports all Windows, macOS, and Linux systems. If you’re using Edge and want to learn how to block or disable extensions from being installed and help protect against risky apps, the steps below should show you how to do it.
By default, Microsoft Edge allows users to install extensions. Extensions are good and can be helpful. However, installing extensions from an untrusted source can harm your computer and steal your information.
This can lead to password breaches in some environments and may go against environmental policy. If you want to disable or block your users from installing extensions in Microsoft Edge, continue below.
To get started with blocking extensions in Edge, follow the steps below:
Disable Extensions in Edge
To block extensions in Edge, open Microsoft Edge and click the 3 horizontal dots ( . ) at the top right corner of your screen, as shown in the image below.
Then select Extensions.
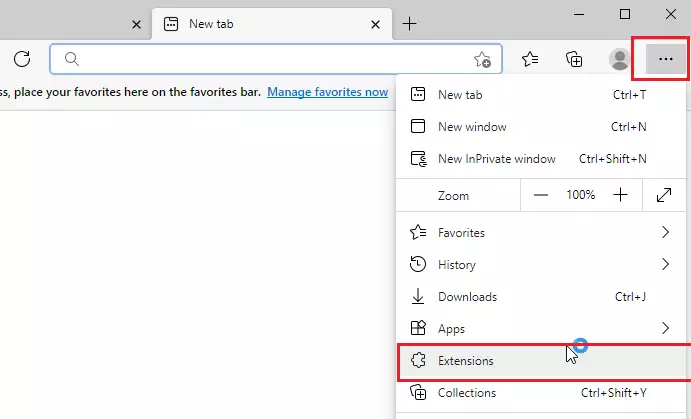
Or you can simply type the URL below in your Edge browser and press Enter to get to the Extensions page.
edge://extensions/
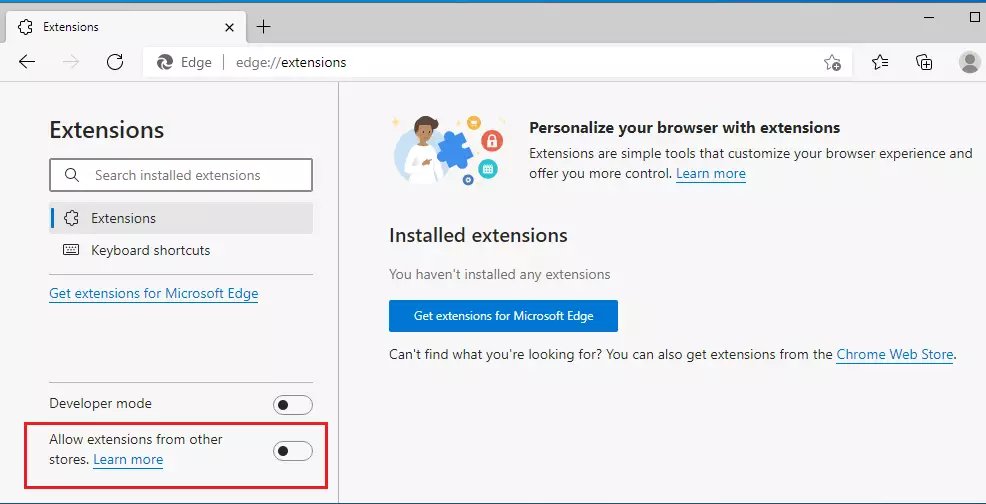
Look at the bottom left corner on the Extensions page and move the button to Not Allow extensions from other stores.
If you enable this setting, external extensions are blocked from being installed. If you turn off this setting or leave it unset, external extensions can be installed.
Block Extensions in Edge via registry
You can also block or disable extensions in Microsoft Edge from the Windows registry.
You can also turn off this feature via the Windows registry if logged in as an administrator. To do that, use the steps below:
Using the Windows registry is one way to force all users on the system to block or disable extensions from being installed. There are multiple ways to do this in Windows; however, using the Windows registry is the easiest and most effective way.
To enable, press the Windows Key + R on your keyboard to open the run command box. Or use the search function to search for the Run app.
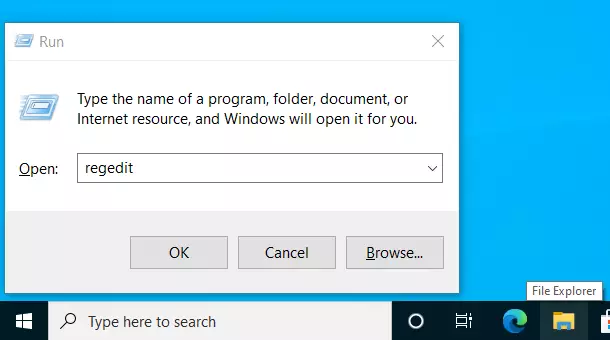
In the command box, type the commands below and press Enter.
regedit
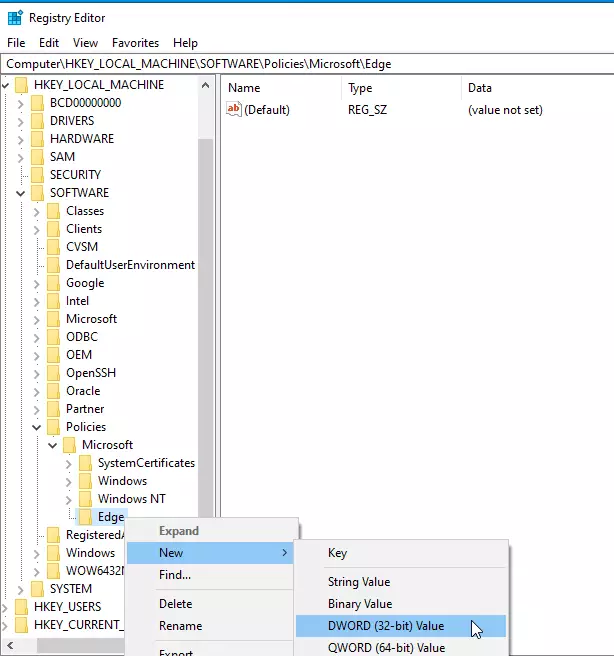
When the Windows registry opens, navigate to the path below. If you don’t see the Edge key, create one.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge
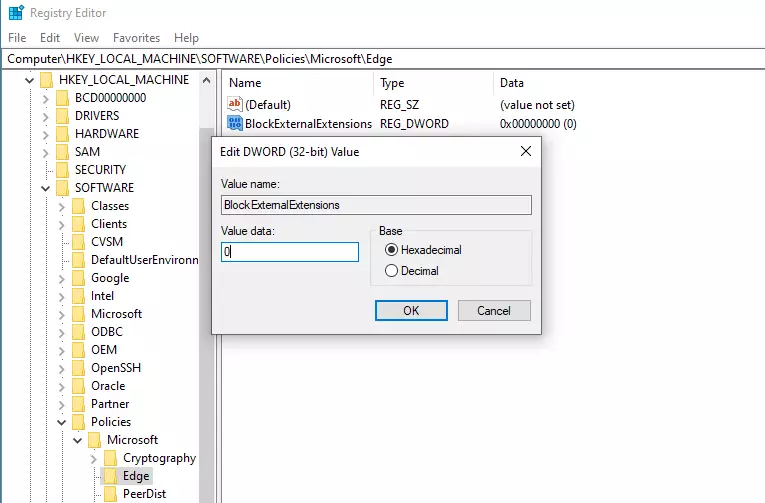
From there, right-click the Edge key and select the New > DWORD (32-bit) Value option to create a REG_DWORD value if you don’t see the existing BlockExternalExtensions value already created.
If you don’t see the Edge key or folder, create one.
Name the new DWORD value as:
BlockExternalExtensions
After saving the DWORD above, double-click it to open. Then, enter the value of 1 to enable. 0 to disable.
(delete) = Default
0 = Always disabled
1 = Always enabled
Next, create a new String value with the name below:
ExtensionInstallBlockList
Then, change the value data to “*” to block all extensions not on the approved list.
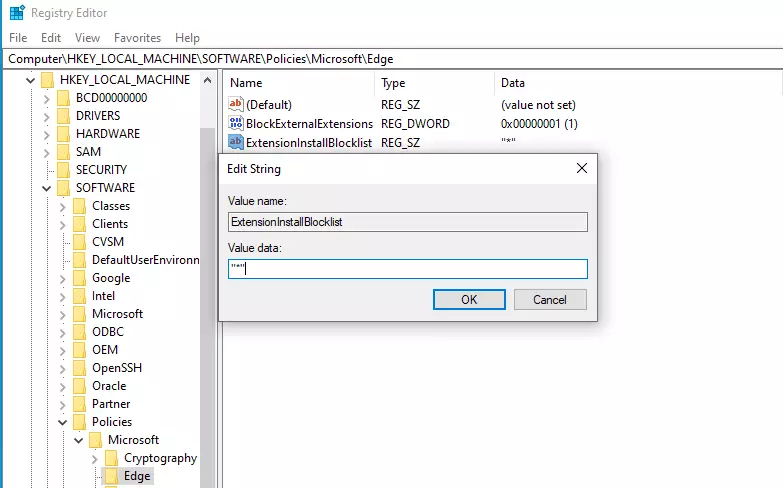
By default, all extensions are allowed. However, if you block all extensions by setting the ‘ExtensionInstallBlockList‘ policy to “*,” users can only install extensions defined in this policy.
List specific extensions that users can NOT install in Microsoft Edge. Use “*” to block all extensions not explicitly listed in the allow list.
Users can install any extension in Microsoft Edge if they don’t configure this policy.
That should do it!
Conclusion:
- Blocking external extensions in Microsoft Edge enhances security and protects sensitive information.
- Using the built-in settings and Windows registry provides flexibility in managing extension installations.
- Administrators can enforce policies across multiple users to maintain a secure environment.
- Regularly review and update the list of allowed and blocked extensions to adapt to new threats.
- Following these steps can help maintain compliance with organizational policies and safeguard user devices.


Leave a Reply Cancel reply